SAP Security Features
Task 1
Task 2
Alphabetic list of activities and their recurrence by selected users:
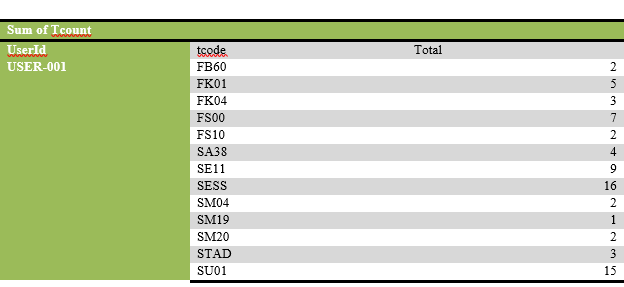
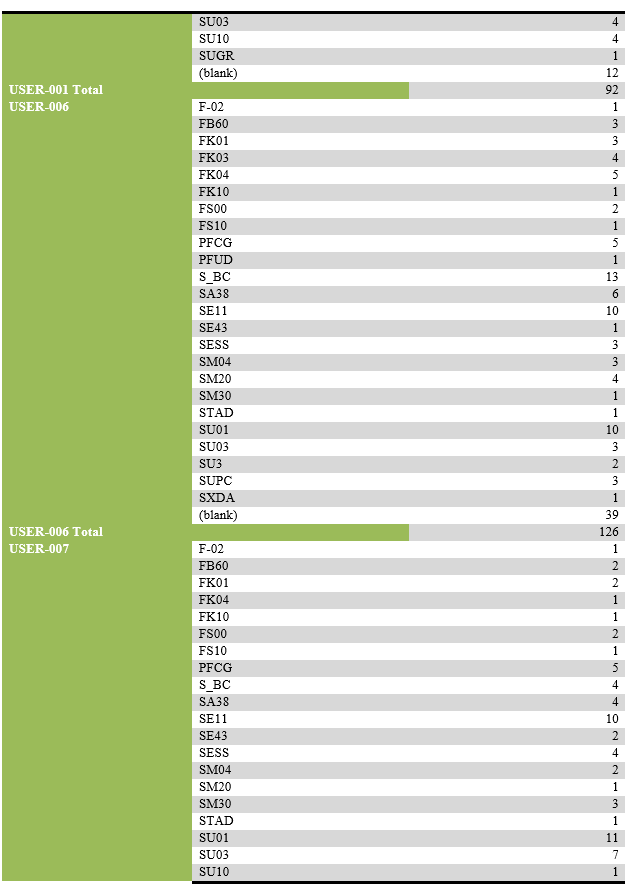
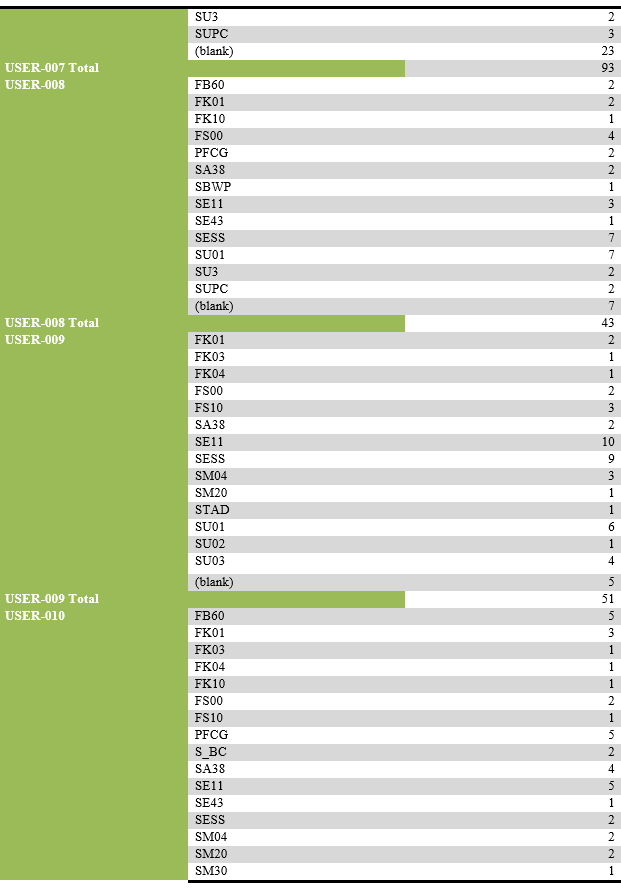
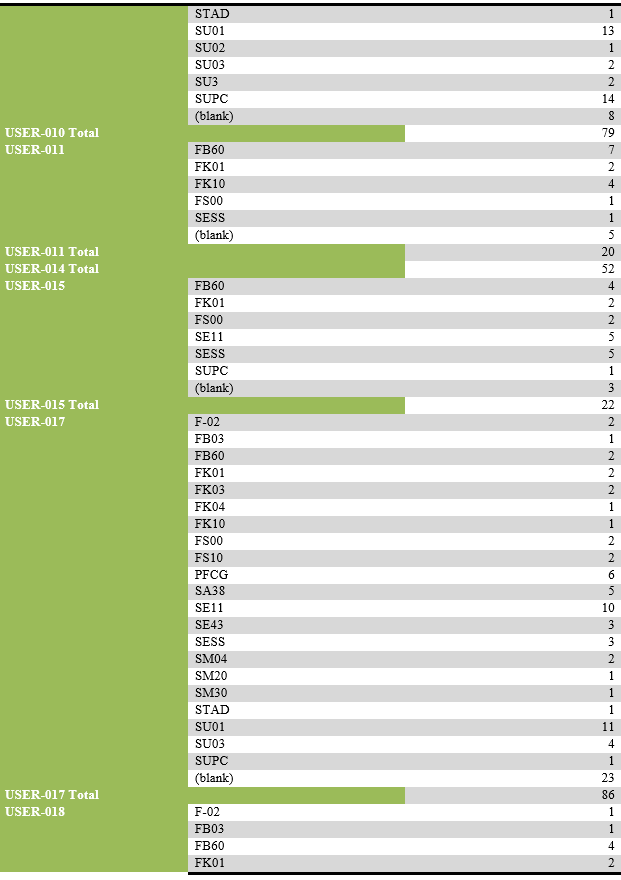
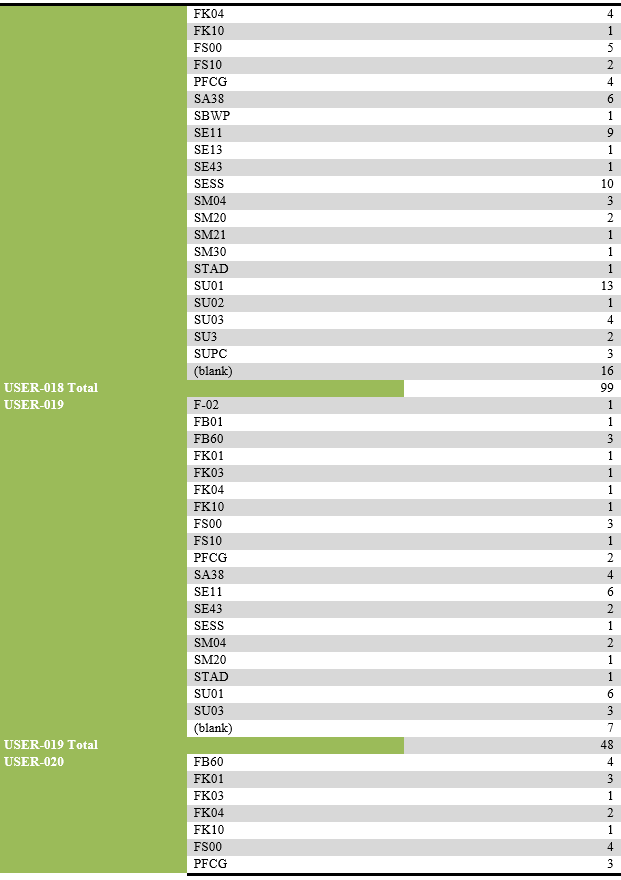
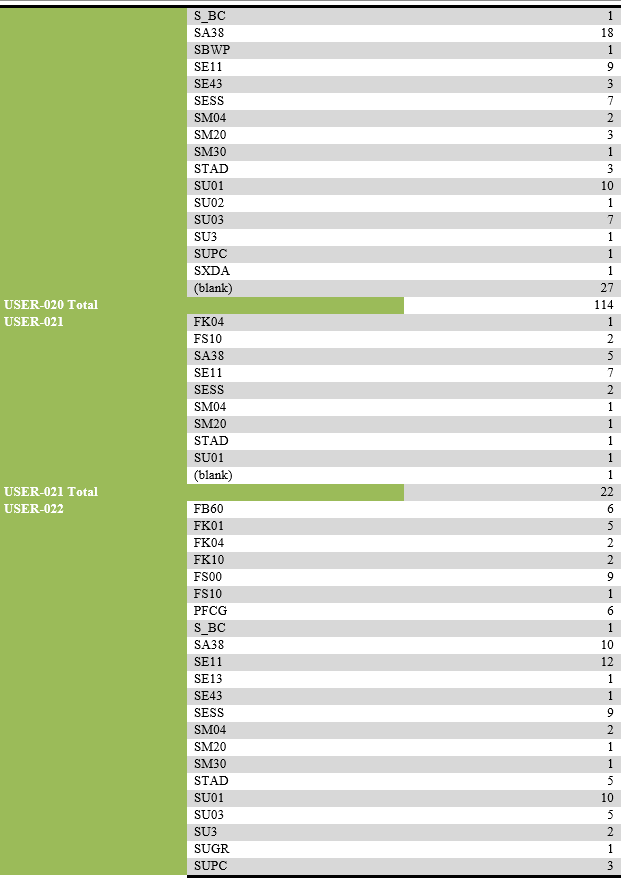
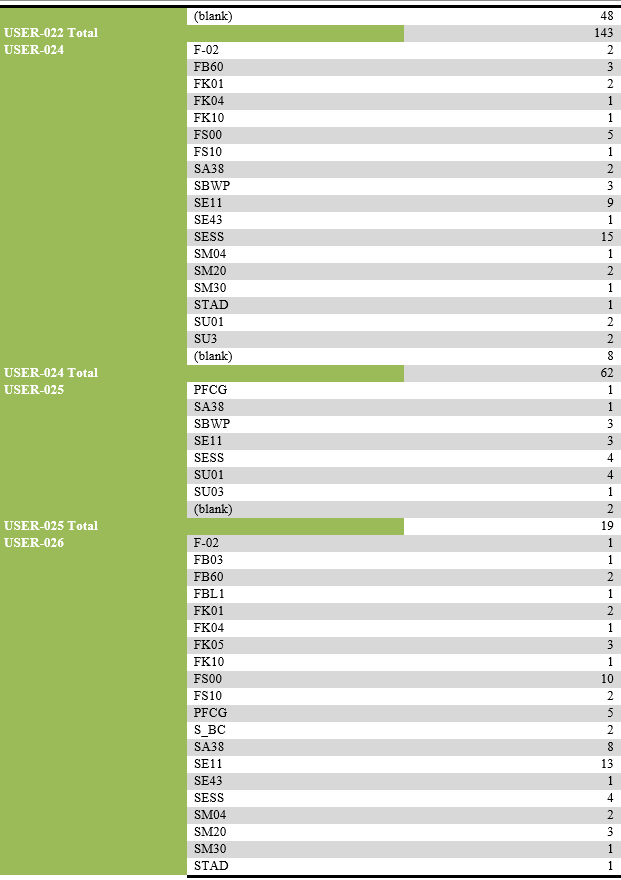
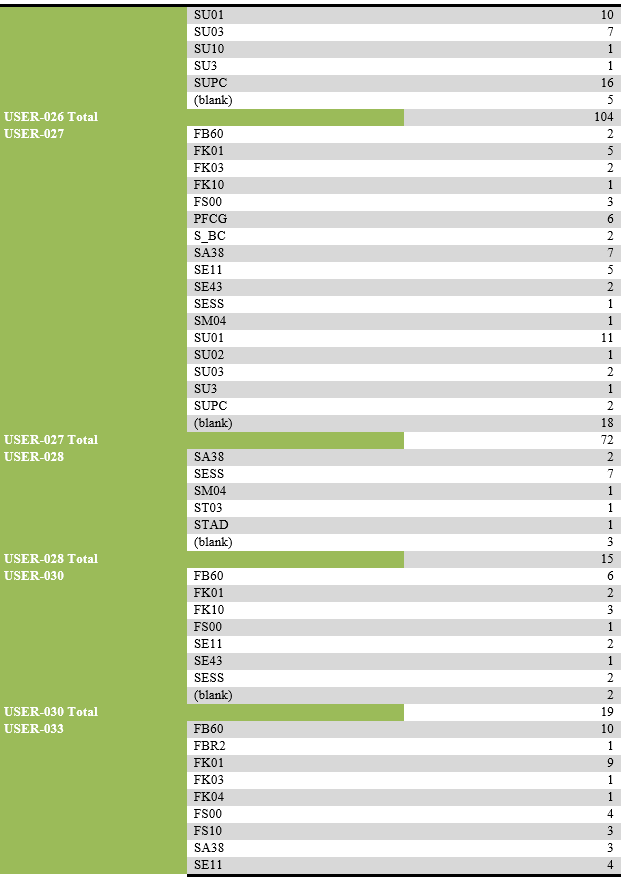
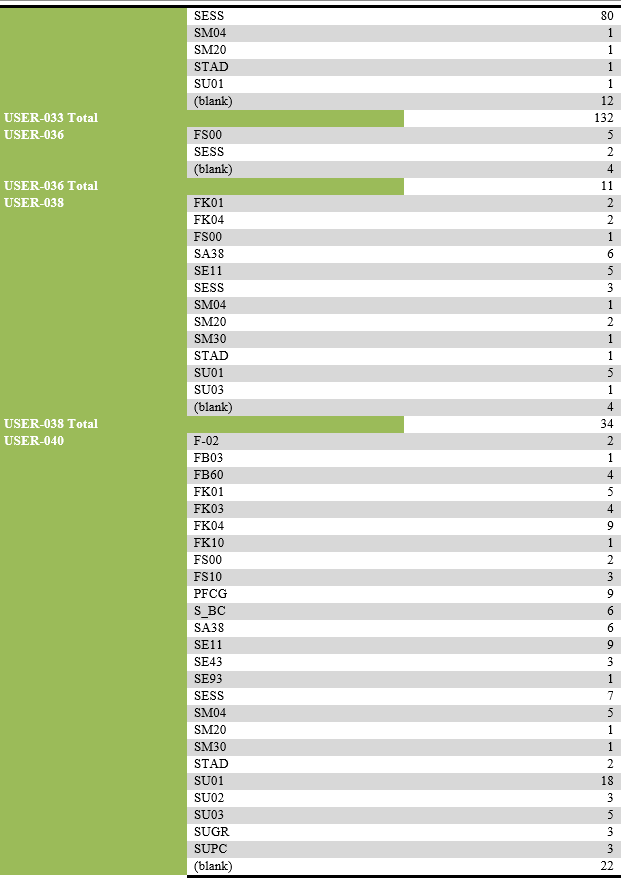
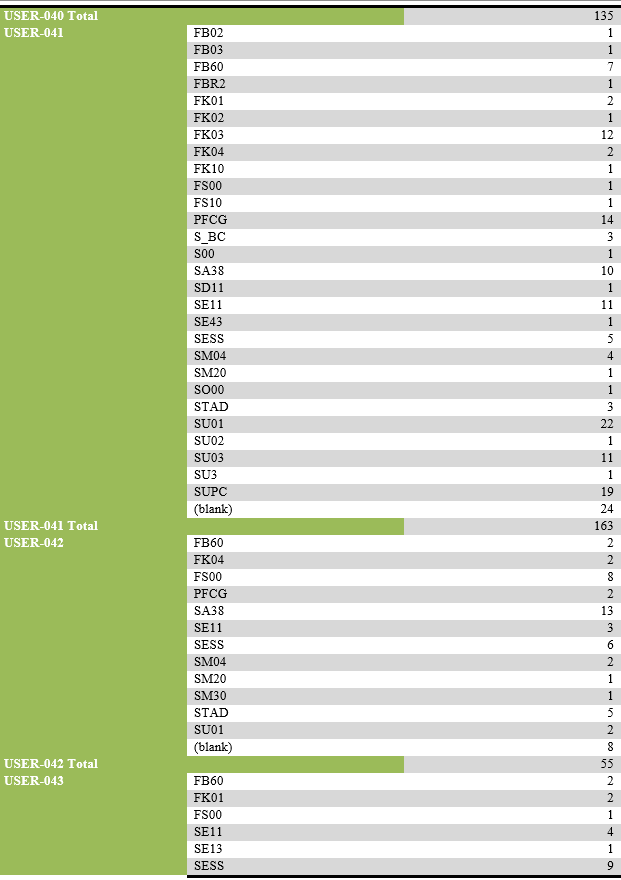
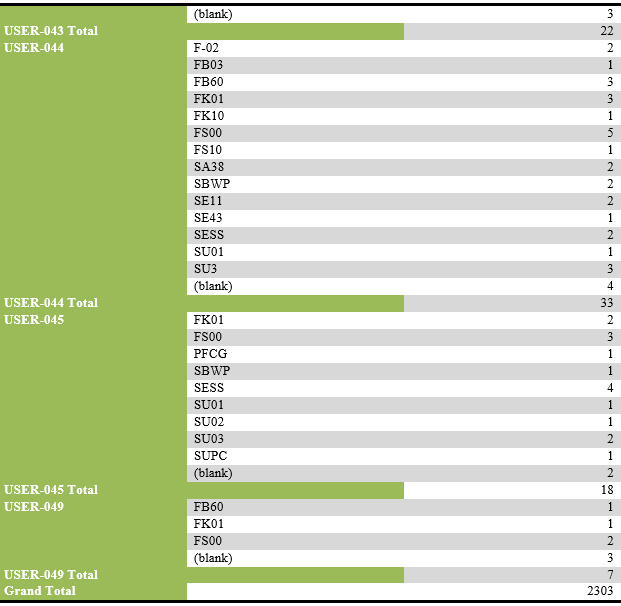
List of users performing unsuccessful activities.
- USER-001
- USER-002
- USER-003
- USER-004
- USER-005
- USER-006
- USER-007
- USER-008
- USER-013
- USER-014
- USER-015
- USER-017
- USER-018
- USER-019
- USER-020
- USER-021
- USER-022
- USER-024
- USER-025
- USER-026
- USER-027
- USER-028
- USER-030
- USER-040
- USER-041
- USER-042
- USER-043
- USER-049
List of transaction codes performed, with their frequency by each user.
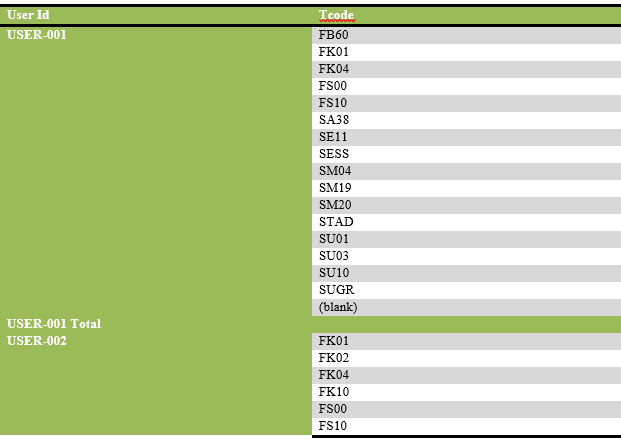
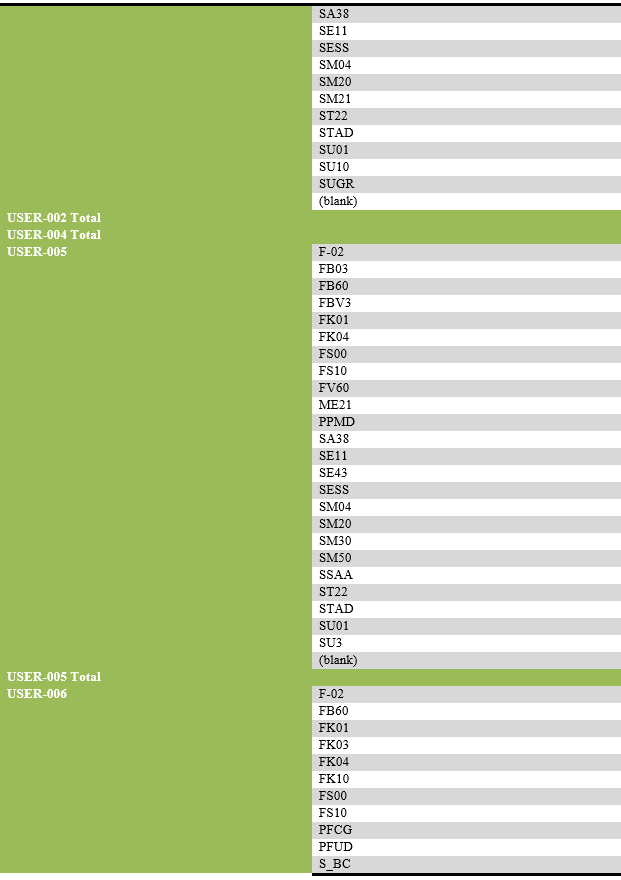
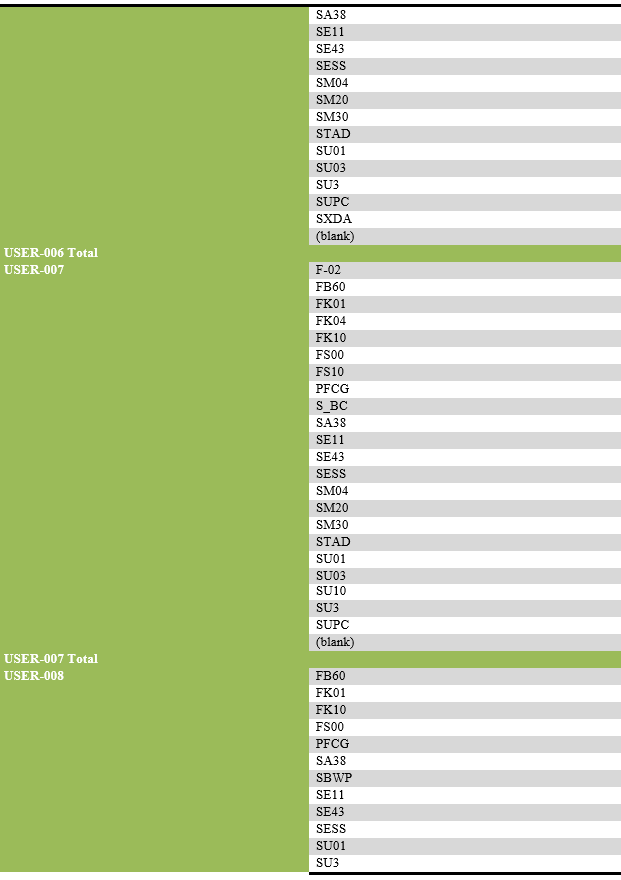
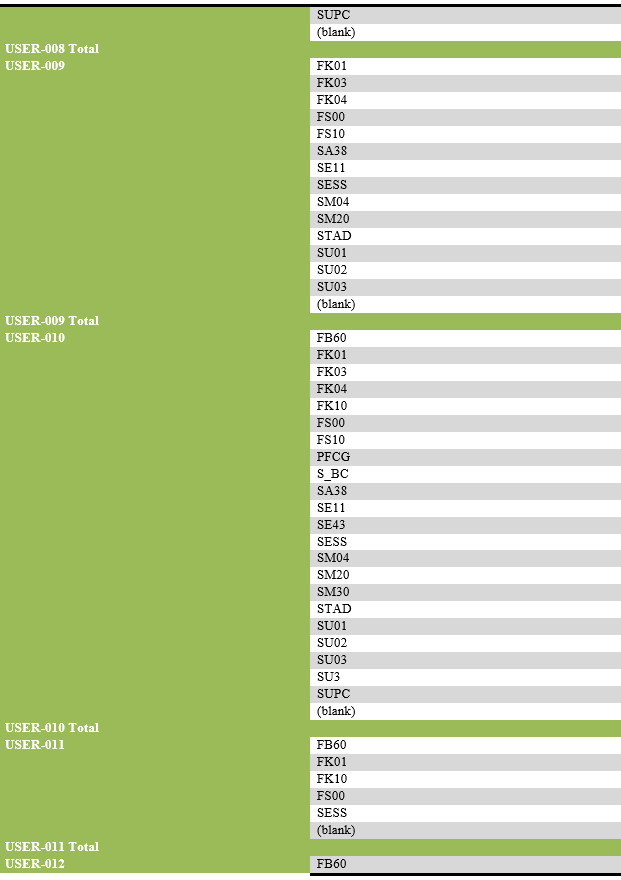
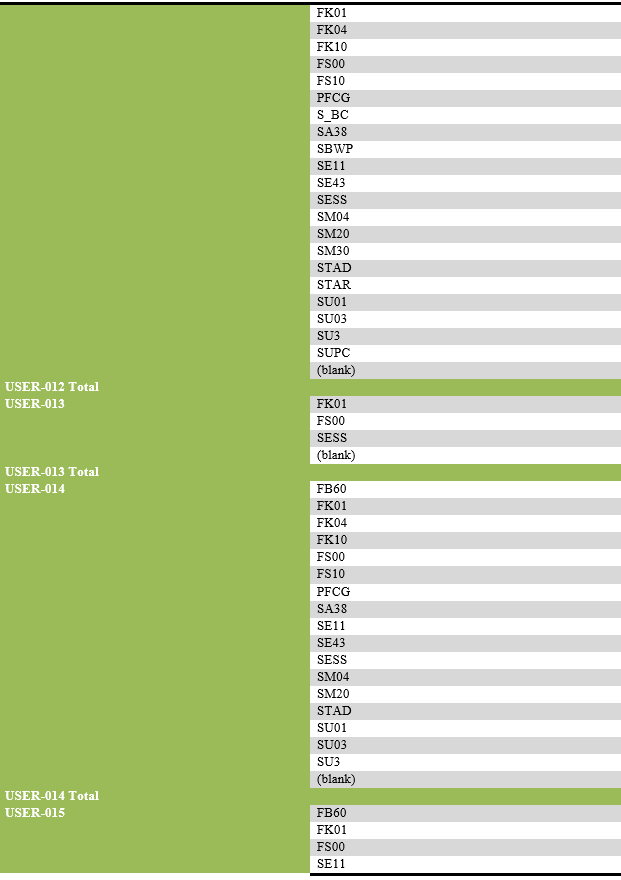
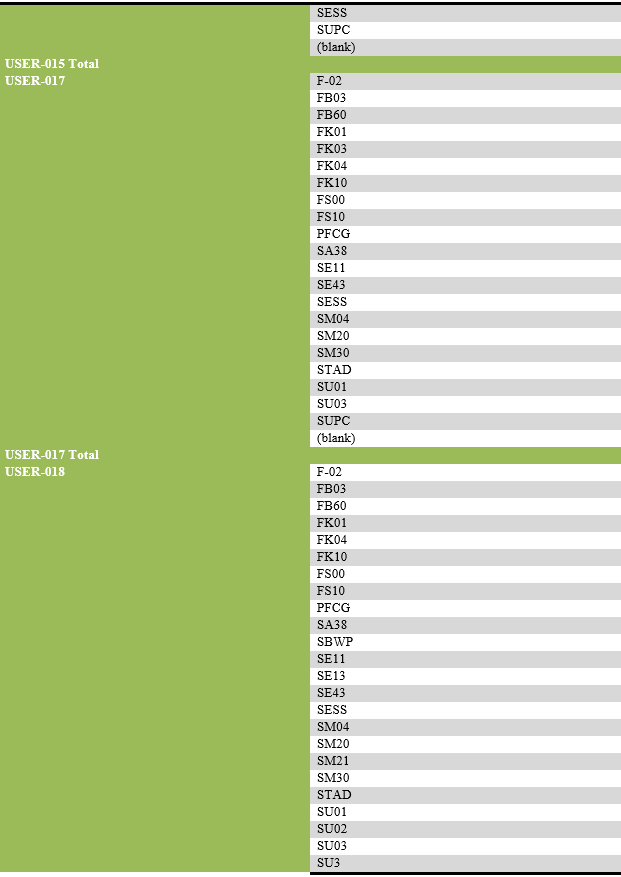
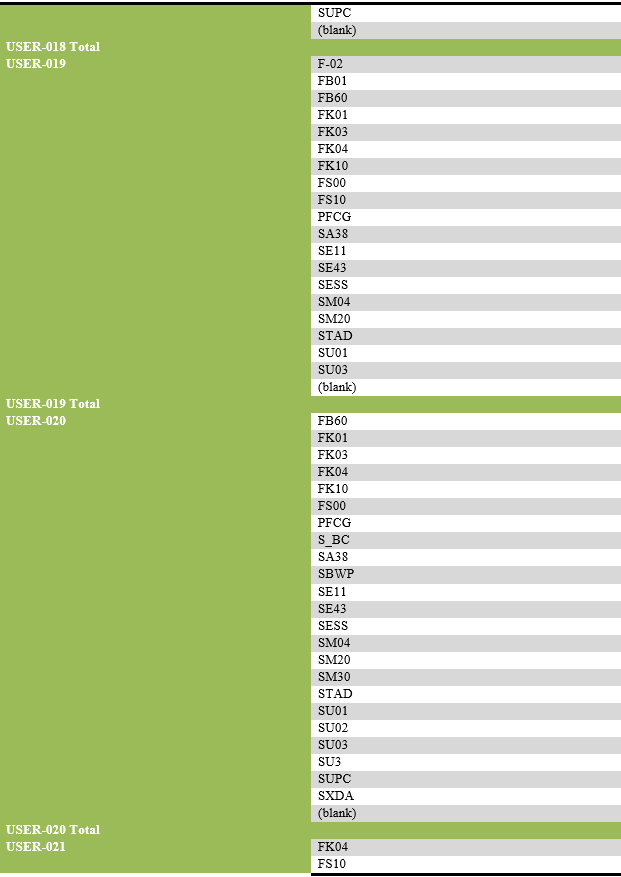
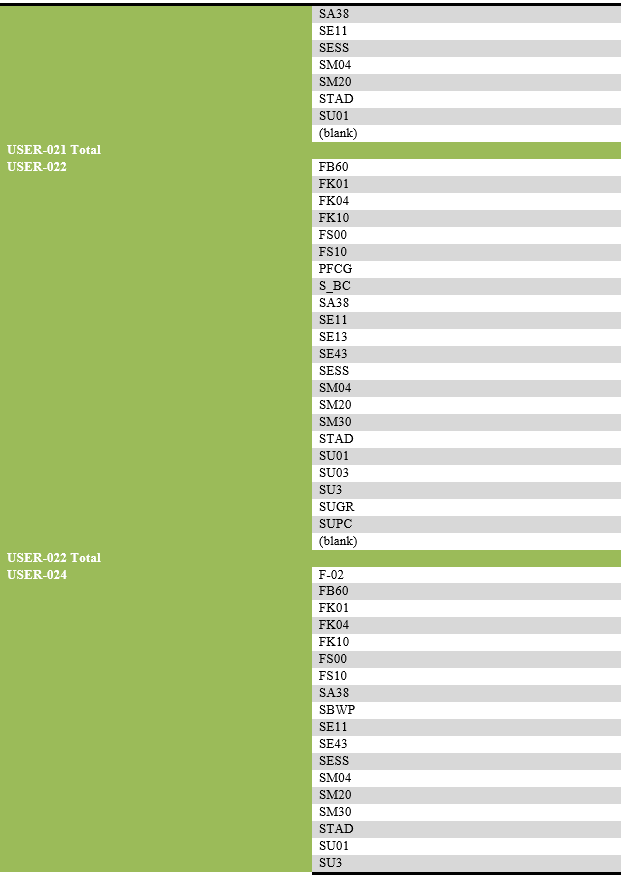
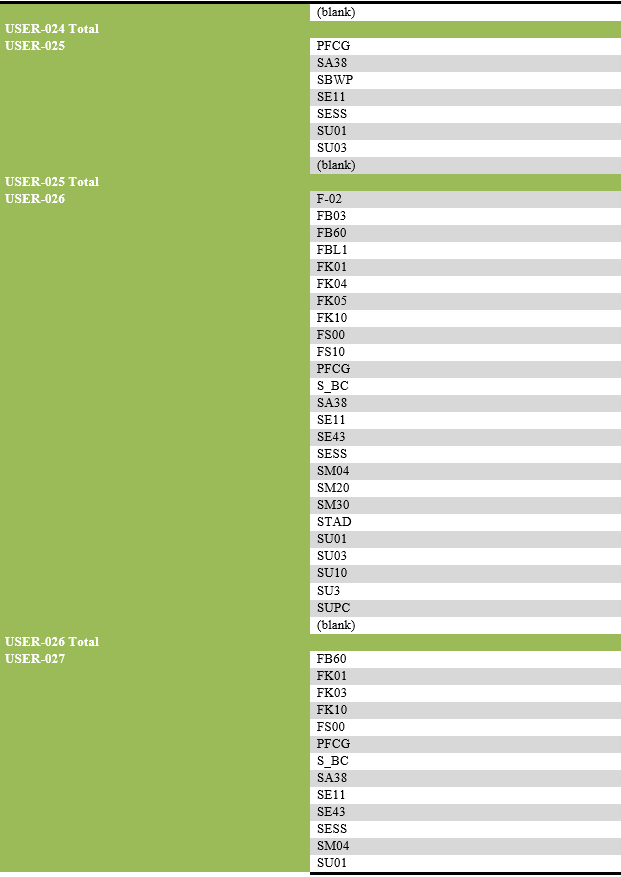
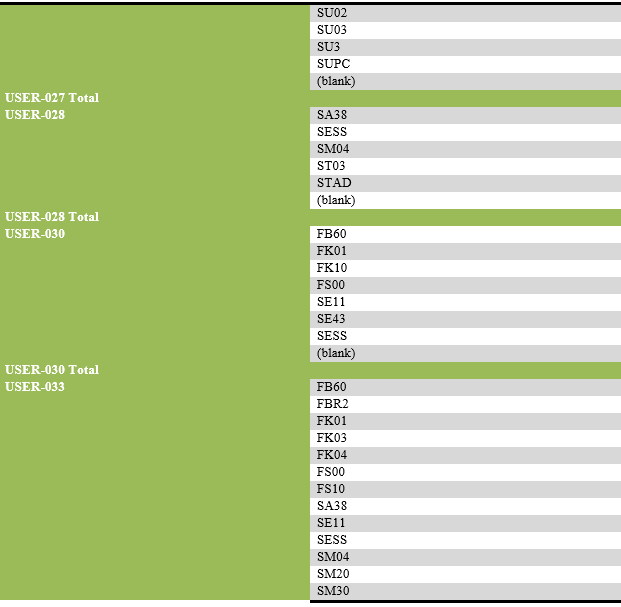
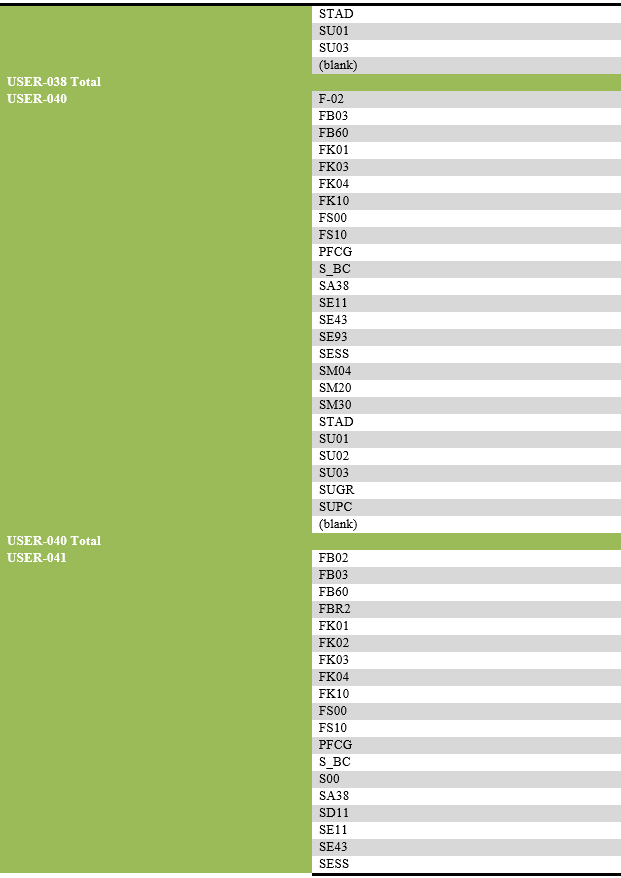
List of users engaging in security-related actions
- USER-015
- USER-017
- USER-018
- USER-020
- USER-022
- USER-025
- USER-026
- USER-027
- USER-030
- USER-033
- USER-034
- USER-038
- USER-040
- USER-041
- USER-045
- USER-046
- USER-047
- USER-048
- USER-049
Top 10 users in terms of frequency of activity
- USER-011
- USER-012
- USER-015
- USER-017
- USER-018
- USER-020
- USER-024
- USER-026
- USER-030
- USER-033
- USER-009
- USER-010
- USER-011
- USER-015
- USER-017
- USER-019
- USER-020
- USER-022
- USER-024
- USER-026
- USER-027
- USER-028
- USER-030
- USER-033
- USER-036
- USER-037
- USER-038
- USER-040
- USER-041
- USER-045
- USER-048
- USER-049
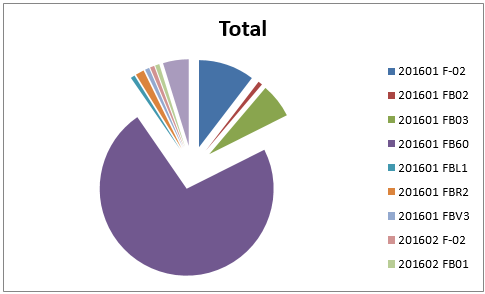
Chart
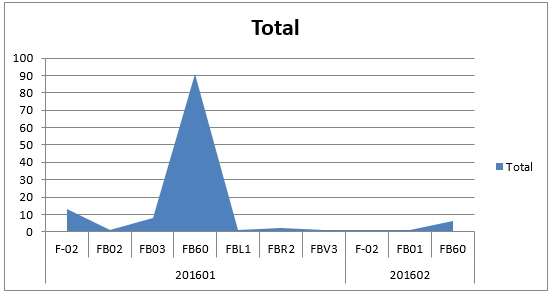
Plot
Task 3
These frameworks portray how the SAP/R3 must manage their security protocols in a proficient manner with parameters. These steady facilities, in addition to the certain very important settings for the whole route of exploits, which must be controlled by SAP Security structures. These ambits shall be enacted to jug understanding high up the operation of the framework. These ambits shall perform SAP works placidly on the client equipment, various machine stages.
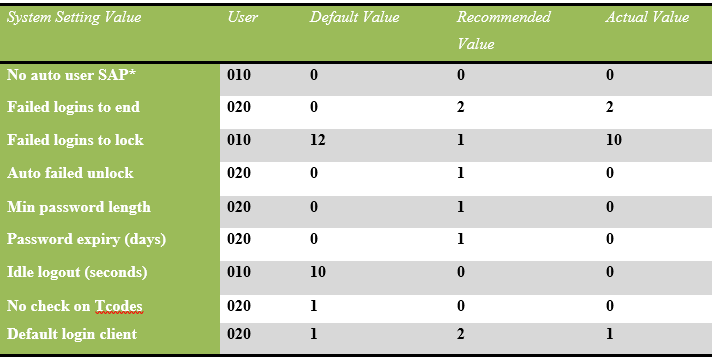
Recommended Settings
There are different assaults to SAP passage, for example, running working framework orders without validation. Limit access to SAP passage by appropriate system controls both inside and remotely. On the off chance that business case exists for client systems to utilize RFC correspondences in view of uses, for example, BEx (Business Explorer), apply legitimate security arrangement on the SAP passage for limiting TYPE E and TYPE R associations. If it’s not too much trouble allude to secinfo, reginfo setup for more data. This shall guarantee that SAP scene is free of powerless or default passwords
SAP frameworks contain hundreds or a large number of clients. A solitary bargained record can bring about issues for whatever remains of the scene. After SAP frameworks are arranged for legitimate secret word approach, we prescribe running watchword reviews on SAP frameworks intermittently to avoid frail passwords, for instance, Welcome01 to be available. Albeit such passwords can be secret word approach agreeable, please recollect that “consistent” does not signify “secure”.
Security Recommendations
- Handicap or limit access to web administrations, for instance, SOAPRFC as well as WEBRFC. These administrations permit RFC correspondence over the Internet.
- Handicap the invoker on SAP R/3 frameworks to keep aggressors from bypassing your framework security controls.
- Any application superfluously accessible expansions presentation which results in raised danger.
Maintain SAP GUI constantly
SAP R/3 system will discharges security fixes each month. That is why, always setup appropriate patch administration arrangements both for the SAP applications and other customer segments, for instance, SAPGUI.
Secure the private key store for insurance against Single Sign-on assaults :
- SAP records contain delicate data which gives an aggressor a chance to make legitimate framework tokens. With these legitimate security tokens, aggressor can interface with remote frameworks as any client WITHOUT A PASSWORD. The tokens are typically legitimate until the end of time.
- Ensure SAP records with legitimate working framework security controls. Secure access to tables, for instance, USER _40D by putting them to a separate table gathering and changing SAP approvals in like manner. Confine executing of OS summons from applications by securing the passage and important application segments. This shall present a normal key substitution process.
Vulnerabilities that Reside in the System
The vulnerability stays in the SAP application layer which means it doesn’t depend on the database application and operating system that actually supports the entire SAP system.
Misuse of SAP R/3 security give unauthentic access to the remote attackers enabling them to directly affect major SAP platforms while having the proper control over the business information and processes on these systems. It also give the access to other potential systems linked with the SAP.
In order to diminish this liability from the SAP, it is recommended that users and administrators implement SAP Security Notes as well as disable the access to any unauthorized user.
Users and SAP R/3 administrators must manage these User default value causing vulnerabilities:
- Describe detailed security guidelines for the system and continuously keep the track of the system for any violations and resolve any noticed deviations.
- Scan the entire system to find any vulnerabilities like missing security blotch and unwanted, threating system configuration.
- Check all systems for noxious or immoderate user
- Examine systems for pointers of compromise resulting because of the abuse of vulnerabilities.
- Analyse and identify the security settings of SAP interfaces among applications and systems to understand the risk presented by these trust relationships.
- Supervise systems for suspicious user behaviour, including both privileged and non-privileged users.
- Apply security intelligence on brand new vulnerabilities improve the security conventions against cutting edge targeted attacks.
Watchword Security Settings:
System format parameters will portray the most diminutive length of a watchword nearby the repeat with help of which customers have the chance to modify passwords.
- Sign-in smallest mystery key length: The base is four characters notwithstanding the most raised seven characters.
- Sign-in slip time: measure of days ensuing to which a watchword ought to be changed. This will allow customers to keep up their passwords with no time limit and likewise leaves the set worth to be default i.e. 0.
To divert utilization of an unmistakable mystery key, experience table USER_40. Keep up this table with trade T30. In USER_40, you may likewise broadly recognize expelled passwords.
For instance:
- 467* in table USER_40 forbids a couple of mystery word which start with the game plan 467.
- *990* forbids a couple of mystery word which join the course of action 567.
- DC? Denies passwords which start with DE notwithstanding have an extra character, for instance, DED, DEE, and furthermore DEF.
- Chiara, F. (2001). Predicting the implementation effort of ERP projects: empirical evidence on SAP/R3. Journal of Information Technology, 16, pp. 33-48.
- Riebel, P., Sinzig, W., and M. Heesch (1992). Fortschritte bei der Realisiering der Einzelkostenrechnung mit dem SAP-System [‘Progress in the realization of ‘Einzelkostenrechnung’ with an SAP system’ – in German]. Controlling, März / April, pp.100-105.
- Bhavani, Thuraisingham and Wei, She (2007). Security for Enterprise Resource Planning Systems. Technical Report UTDCS-33-07.
- Van de Riet, Janssen, and Gruijter (1998).Security moving from database systems to ERP systems. 9th International Workshop on Database and Expert Systems Applications(DEXA’98) 273-280.
The company offer their custom writing services around the globe covering major countries like the UK, USA, UAE, Australia, Hong Kong, Malaysia, etc. Whether, it is Christmas, New Year, summer vacation, winter vacation, or any other holiday, the experts work all 365 days to help students. Another advantage of availing SAP homework and assignment help service from the BookMyEssay is their services comes at an affordable price. The writers are experienced enough to easily write on any title including cryptic or complicated assignment topic. With 24*7 students support and the team of professional writers BookMyEssay is the ideal solution for students.


